-
Notifications
You must be signed in to change notification settings - Fork 76
Azure Function, Multi Region, Local Cache support
Originally the site-extension would only work for single region web app sites and/or web apps without local caching enabled because it would use the local file system to store the challenge file. The challenge file is a file that the web site must be able to present to Let's Encrypt to prove ownership of a domain.
In version 0.8.9 this limitation has been resolved. The site-extension now supports writing the challenge file to an Azure blob storage account that you define. However when using this approach your application is responsible for serving the challenge file. Let's Encrypt always requests the challenge file from http://yourdomain/.well-known/acme-challenge/<random-file-name> it is your responsibility to ensure that such requests response with the text content from the file in the blob storage container.
To enable this new behavior you must add an application setting named letsencrypt:AuthorizationChallengeBlobStorageAccount, this settings should contain the azure storage account connection string of storage account you want to use. The default behavior when the setting is present, is that the site extension will write the challenge file to a container named letsencrypt-siteextension to a path .well-known/acme-challenge/<random-file-name>. If you want to use a different container you can define that by using the app setting letsencrypt:AuthorizationChallengeBlobStorageContainer you can use this to target the $web container if you have static hosting enabled in the storage account. Per default the site-extension enables public blob access to the container.
Assume that you have an Azure Function App for which you have installed the site extension, for some reason you want to save the challenge file saved to azure blob storage, so you add the letsencrypt:AuthorizationChallengeBlobStorageAccount application setting.
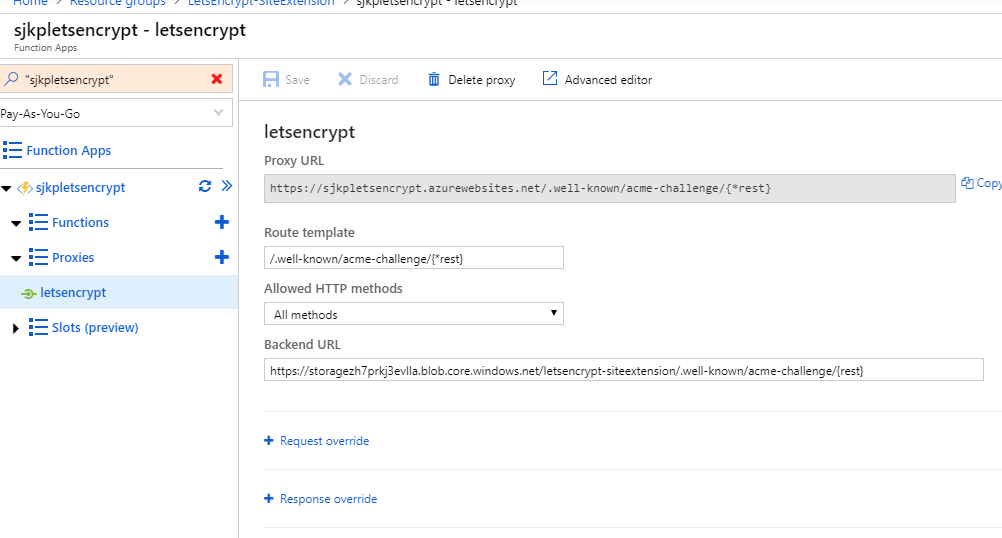
Once you have done that you need to ensure that your function serves the challenge file, before you can request the first certificate. The simplest way to do that is to setup an Azure Function Proxy that redirects request from /.well-known/acme-challenge/{*rest} to your storage account.
The code if you want to do it with an proxies.json file is
{
"$schema": "http://json.schemastore.org/proxies",
"proxies": {
"letsencrypt": {
"matchCondition": {
"route": "/.well-known/acme-challenge/{*rest}"
},
"backendUri": "https://<REPLACE-WITH-YOUR-STORAGE>.blob.core.windows.net/letsencrypt-siteextension/.well-known/acme-challenge/{rest}"
}
}
}